Low Code, No Code can make Salesforce development faster, but it comes with risks.

View and download the full article or read it below.
Rise in Low Code, No Code
The rise of Information Technology as a key driver of productivity and innovation over the last 40 years has been astounding. Two of the most remarkable evolutionary trends in the last 15 years are the rise of Software as a Service (SaaS) and Low Code, No Code platforms. Software development and deployment are no longer constrained as they once were.
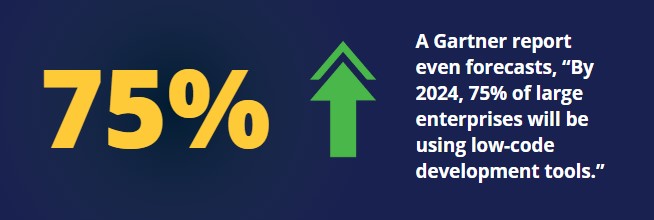
While in 2020, less than 25% of new apps were developed using No Code, Low Code, Gartner predicts that by 2025, 70% will utilize this means.
From a systemic perspective, software consumers can rely on professionally managed platforms with high availability that are constantly kept up-to-date. These systems are incredibly robust and allow organizations to configure systems and processes to meet their needs.
Moreover, platforms have been empowering their users by creating dynamic ecosystems that allow their users to extend their base platform by integrating 3rd party applications or by developing custom code.
What is Low Code, No Code?
One of the leading business software solution platforms, Salesforce, exemplifies these awesome capabilities. Their platforms began as a SaaS solution, but they are continuing to expand with Low Code, No Code solutions.
Salesforce allows Administrators to have control over practically everything, from the user interface to data security. They can create data structures and input/output flows that match the specific needs of their organization. They can even integrate applications that extend the functionality of their Salesforce instance.
All of that power comes without writing a single line of code, hence the “No Code” label. With the help of a Developer, organizations can write their own code to extend their Salesforce capabilities. This might be as simple as a snippet of Javascript that validates user input or as complex as a large software project that processes data and kicks off critical business flows.

At some point, “Low Code” is defined within the eye of the beholder, but in a larger context we are referring to the concept that a developer can build upon a platform and extend core software and security infrastructure quickly.
Why There's a Shift
Extending the power to shape and develop software to more users unleashes an organization’s capabilities as it lifts the constraint of needing “Developer expertise.” This phenomenon is often described as Digital Transformation, where technology not only changes the way we conduct business but also the very business that we conduct.
Many have commented that this transformation can often be compared to a snowball careening downhill, gathering speed and mass with each revolution.
Risks of Low Code, No Code
There are important risks of which to be aware. Most fundamental, these new processes and tools are developed in response to the fact that organizations are storing information online, in both significant volume and value.

Widgets that are associated with Low Code, No Code like Robotic Process Automation (RPA) are used to manipulate data and change it. The benefit of these kinds of tools lies in their automation, but can come at the cost of having fewer controls for the kind of data that it should/shouldn’t be transmitting. There is a need for these kinds of tools to be monitored from a Governance, Risk & Compliance (GRC) perspective.
In a recent article by The New Stack, Charles Lamana, Corporate Vice-President for Business Apps and Platforms at Microsoft, recommends being “proactive with your low-code strategy. You can define policies and rules and governance, and have a strong posture around your data,” said Lamanna. “Because managing data access to your data, whether it’s at the database or at the API layer, is the most sensitive information that you can manage,” Lamanna added.
Certainly, financial or health data has long been understood to be particularly sensitive and there are strong industry and regulatory standards that govern them, such as PCI/DSS or HIPAA. But, we are also seeing more attention to broader concerns of privacy and use through the rise of GDPR and CCPA.

Another consideration is that as the platforms and code libraries become more entrenched and popular across an industry, risk factors increase. “Security through obscurity” has long been debunked as foolish and ill-advised, but the reverse is not true.

Software that has a substantial user base will likely attract attention from those that wish to identify exploits. Finally, Digital Transformation ultimately means that users are likely interacting with many different systems throughout their work day.

Some systems may have more valuable information than others, but a breach of a single point of your security perimeter puts your entire enterprise at risk.
How DigitSec Solves for Salesforce Security In A Low Code, No Code World
At DigitSec, we are providing an important tool that companies can use to manage these risks. Our security scanning allows organizations to analyze their Salesforce Orgs for potential security risks on both the No Code dimension and the Low Code dimension.
By automating analysis and monitoring, organizations can integrate checks into their development lifecycle and address potential security issues during testing.
In this way, they can be proactive in avoiding the introduction of security vulnerabilities. Moreover, constant vigilance also allows them to be incredibly responsive when new exploits are identified in 3rd party integrations or libraries. Our platform allows organizations to pace their security posture to their digital transformation acceleration.